There is a misconception that I have come to see in my time working in IT that is more prevalent than any other: We are safe because we are small. Small businesses feel like they are shielded because they are small and not a known or big named target. This
Read MoreFirewalls have been around for about 20 years now. They emerged more prominently as the Internet became commercialized and more networks and people connected--which meant more targets. Having a firewall is pretty much a mainstay today. You will find dedicated firewall appliances or Internet routers with so-called firewall capabilities. These
Read MoreCompanies and people often "place" files on storage like S3 and DropBox and it doesn't get cleaned up after the files are used, leaving the data and the privacy of the subjects of that data to be vulnerable like this study proved. Instead of storing the data for temporary use,
Read MorePasswords are becoming increasingly painful to remember. Creating them and remembering them for every single thing we are signed up to can be tedious and with reports of sensitive data being compromised due to hackings of reputable companies, the need for a password manager has never been greater. Here's an article
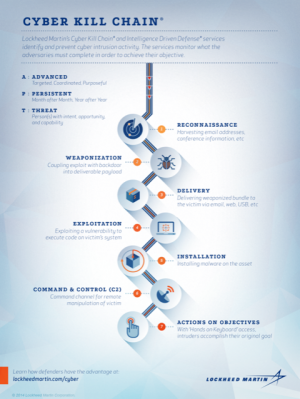
Read More"Kill Chain," was a term originally used by the military to define the steps the enemy uses to attack a target. In the same way, a "Cyber Kill Chain," is a similar notion but relates to cyber-based attacks. It's a process that centres around understanding each of these stages so
Read MoreThe main reason for using USB sticks is to transfer data from one computer to another. It may not necessarily be to even give to someone else, but to take home to do some work or move onto a laptop before going on a business trip. USB sticks are prone
Read MoreEven though we’d like to think we’ve taken all precautions when it comes to securing our business, hackers continually evolve and find innovative ways to find the vulnerabilities in modern business networks. Here’s an article by Martin Horan from FTP Today that talks about what you can do to
Read MoreA recent tweet from UK politician Nadine Dorries set cause for alarm. Her tweet was an attempt to defend fellow political Damien Green who was recently in the spotlight for allegedly accessing porn using his government login.
Here is a screenshot of the tweet:
 Read More
Read More
Here's a great article from Time by Jeff John Roberts on the benefits of cloud. Because we are in a content heavy world, cloud plays a convenient storage space, however, this also poses it's own security threats - think back to the Jennifer Lawrence incident back in 2014. Read
Read More